FOR SHARE - JULY SNAPSHOT - Access and Usage Policy Enforcement - Two pages description
Early draft
Please be aware that the Data Spaces Blueprint content shared in these pages are a very early draft published on 2023-07-01. The current draft is incomplete and the content might still change.
SAVE-THE-DATE 01-10/09/2023: We will welcome your feedbacks to future improve the Data Spaces Blueprint during the Public consultation that will open on September the 1st 2023 until September the 10th. Please mark these dates in your calendar and get ready!
Overview
The purpose of this document is to define the scope of the “Access and Usage Policy Enforcement” building block, as part of the taxonomy for data spaces defined in the Data Spaces Support Centre.
This building block (building block) is essential for enabling data sovereignty in data spaces, it is the technical foundation. As building on legal, data cannot be sold, because the ownership does not change. Thus, access and usage are the units of business transactions within a data space as part of a data product offering. As a result, it is of major importance for every business operation within a data space. Furthermore, this building block may be directly correlated with the Legal Building Blocks, as some domains may be effected by concrete regulations for the enforcement of policies. We hypotize that there are multiple archetypes of this building block based on the interaction pattern of data sharing. Therefore, we will also address the unique challenges of policy enforcement related to personal data. In summary, the purpose of a data space is about controlled data sharing, thus, it cannot be realized without policy enforcement.
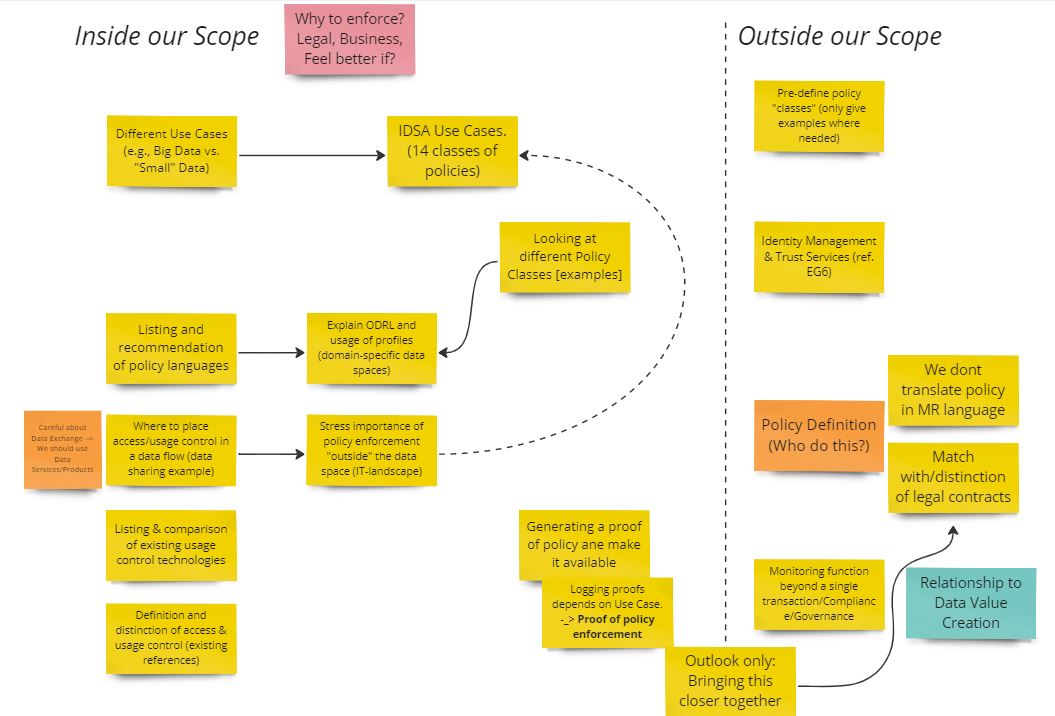
Therefore, we define the scope of this building block as the technical enforcement of access and usage policies and creating a proof of enforcement. We will define this based on different use cases or policy classes and provide an overview of different data sharing examples, in which we determine the point of enforcement within the data flow. We will not consider policy definition and the matching with/distinction of legal contracts. However, this is of importance for this EG, thus, we will closely collaborate with the respective EGs.
Key elements
As mentioned, the objective of this building block is to materialize data sovereignty by enforcing defined access and usage policies with data spaces. The building block is necessary for all kinds of transactions, be it data or services. In particular, we propose data processing services as a unique form of transaction object, as they are unique components taking data in and sending data out. From a legal perspective, it makes a big difference whether the services process data on behalf of the data using service or the data provider, or whether they are a unique data controller entity in between. If the latter, this could be reduced (in the context of data spaces) as a combination of data using and data providing entities.
However, based on this, the following types of stakeholders will be considered.
Rights Holder: The rights holder grants access and usage rights to a data user. They can be legal persons, natural persons, or technical entities, such as machines or devices.
Provider and Receiver: Provider and receiver are excecutors of the transactions.
User: Users are granted access and usage of a specific data product offering.
Intermediary: Intermediaries actively or passively participate in data transactions. They are not assigners or assignees of policies. Furthermore, data aggregators and processors are intermediaries.
Key functions
In principle, the following basic functionalities have to be provided. They will be further developed in during the functional specifications phase.
Gathering the relevant information: Decision context
Decision taking/policy engine: Making a decision about access or usage granting.
Generate a proof of of policy enforcement and make it available: The documentation of positive evaluation of policy enforcement is important for trust in the data space. Without evaluating the enforcement, it is not possible to detect fraud and, thus, data sovereignty is neither ensured nor documented.
Dependences and relationships
Dependences and relationships (boundaries to be clarified) with other building blocks (meetings would be desirable at some point in time). However, this list is initial and will be revised and probably extended.
Identity Management & Trust Anchors: Granting access and usage is strongly correlated with identities, as a data space member makes them available to an identity. The evaluation of policy enforcement can be a proof of a credential. It might also be useful to determine verified credentials for members or applications that limit access to certain data products, i.e., only trusted applications can process a set of data products.
Data Value Creation: This building block represents an important prerequisite for Data Value Creation. Foremost, the accounting relies on the actual usage of data. Thus, without enforcing policies and proving this (e.g., logging), it is not possible to account data utilization on a sound data basis. Therefore, a data offering must include proper access and usage policies.
Data Catalogue: In the data catalogue, data definitions are redesigning, which might be needed to define the policies. Catalogue should have also data about the policies.
Business: Data itself is not the saleble unit in data spaces, it is granting access and usage rights. Thus, this building block is a core aspect of operating the business building block. Furthermore, the design of access & usage policies are part of the definition of data products. Thus, they can build on this to define the business impact.
Governance Framework: Governance model and governance framework has already some initial framework for data sharing policies.
Legal: how regulation is enforced by the legal block regarding to the use of data, especially for personell data. For business data this is also valid, since the contractual agreements might encompass specific usage policies. Regarding this, it is important to emphasize policy enforcement “outside” of the data space, i.e. juridical enforcement. However, the distincting/matching of legal contracts and maschine readable policies is out of scope for this building block. Neither we consider the monitoring function with the data space beyond the logging of enforcement of single transactions. Furthermore, the linkage between access and usage policies and legal contracts is of importance for this building block.
Observability: Can take over when a policy could not be technically enforced. Oberservation is a utility of transparency and transparency can be part of the enforcement (proof).
Relevance for the data space
Access and Usage Policy Enforcement is a central component for data sharing. Without this building block, data sovereignty is not easy to achieve. Furthermore, regulations might be not met without this building block, especially regarding to the use of personal data, since most data exchange scenarios for personal data require either consents that must be audited, or personal data access needs to be restricted to parties with appropriate right to access and process.
Scoping overview