Third Party SSO
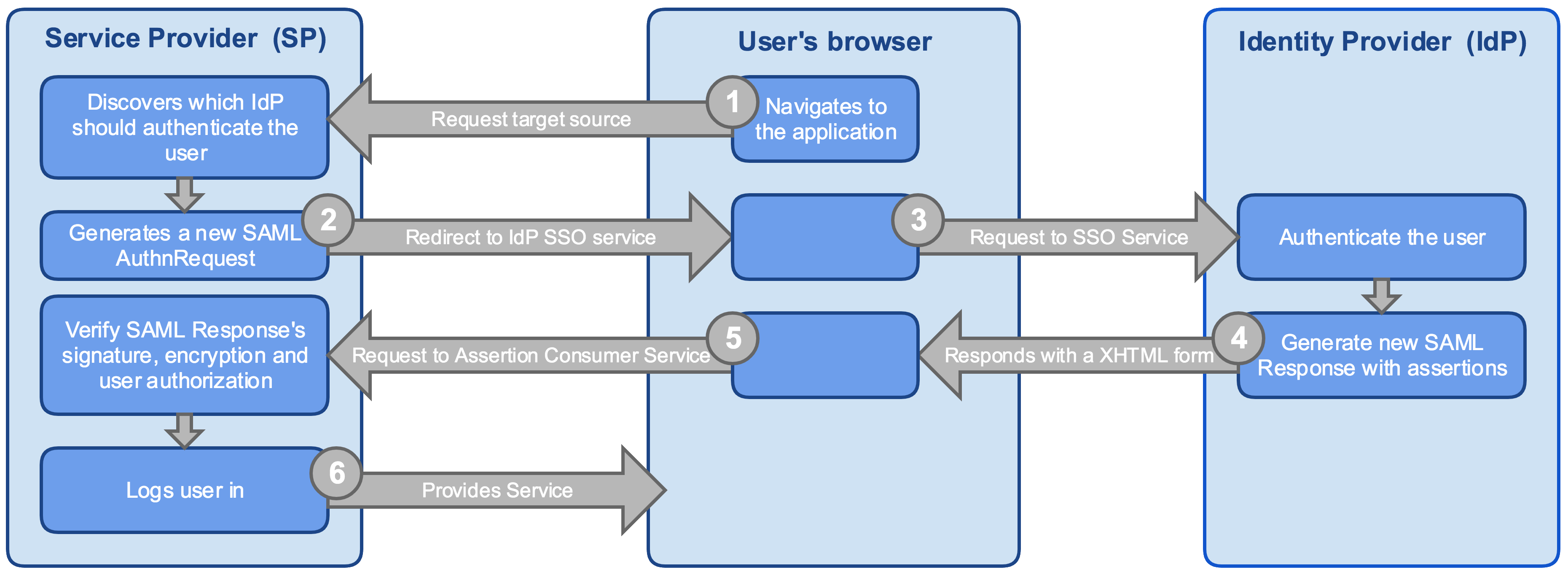
25Our Single Sign-On (SSO) uses the SAML 2.0 standard for exchanging authentication and authorisation between Service Providers (SPs) and Identity Providers (IdPs).
SAML stands for Security Assertion Markup Language. It is an XML-based open standard used to exchange authentication and authorisation data between security domains, in particular, between an Identity Provider (IdP) and a Service Provider (SP).
The standard SAML SSO flow is as follows.
Third Party libraries
There are a number of available third party libraries to make it easier to integrate SSO into your current application. You must make sure that the chosen library supports sha256 for signing.
We recommend the https://github.com/onelogin/php-saml for php applications and https://github.com/hslavich/OneloginSamlBundle for Symfony applications.
For Java application we recommend https://spring.io/projects/spring-security-saml.
For .Net we recommend https://github.com/Sustainsys/Saml2
Private key and certificate
You can generate a key pair with OpenSSL.
openssl req -new -x509 -days 365 -nodes -sha256 -out saml.crt -keyout saml.pemSAML Metadata
The standard defines a metadata document which describes a SAML deployment (including relevant endpoints and X.509 certificate). This will be available at <SAML URL>/saml/metadata. A entity ID will also need to be chosen, we recommend that it should be the URL of the metadata for example https://www.example.com/metadata. During a certificate rollover the metadata will contain two KeyDescriptors. The order of the KeyDescriptors is not guaranteed. The new key should be used immediately but the old key will still work for 14 days. After 14 days the old key will no longer work and the metadata will only display the new key. Ideally the metadata endpoint should be queried daily to ensure keys are always up-to-date.
Sport:80 Metadata
It is important to know that the testing sandbox environments on the subdomains of the test servers have different Metadata to the LIVE production environment.
Example of Idp XML metadata
<?xml version="1.0"?><EntityDescriptor xmlns="urn:oasis:names:tc:SAML:2.0:metadata" entityID="https://sso.sport80.com/saml/metadata" ID="_5cdb44cc66cd321b45a665f64cf07f5e750f621a00"><IDPSSODescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol" WantAuthnRequestsSigned="true"><KeyDescriptor use="signing"><ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#"><ds:X509Data><ds:X509Certificate><-- X509 Certificate --></ds:X509Certificate></ds:X509Data></ds:KeyInfo></KeyDescriptor><SingleLogoutService Location="http://auth.services.localhost/saml/logout"/><NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</NameIDFormat><SingleSignOnService Location="http://auth.services.localhost/saml/login"/></IDPSSODescriptor></EntityDescriptor>
Example of Idp XML metadata during certificate rollover
<?xml version="1.0"?><EntityDescriptor xmlns="urn:oasis:names:tc:SAML:2.0:metadata" entityID="https://sso.sport80.com/saml/metadata" ID="_5cdb44cc66cd321b45a665f64cf07f5e750f621a00"><IDPSSODescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol" WantAuthnRequestsSigned="true"><KeyDescriptor use="signing"><ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#"><ds:X509Data><ds:X509Certificate><-- X509 Certificate --></ds:X509Certificate></ds:X509Data></ds:KeyInfo></KeyDescriptor><KeyDescriptor use="signing"><ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#"><ds:X509Data><ds:X509Certificate><-- X509 Certificate --></ds:X509Certificate></ds:X509Data></ds:KeyInfo></KeyDescriptor><SingleLogoutService Location="http://auth.services.localhost/saml/logout"/><NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</NameIDFormat><SingleSignOnService Location="http://auth.services.localhost/saml/login"/></IDPSSODescriptor></EntityDescriptor>
Example of SP XML metadata
<?xml version="1.0"?><md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" validUntil="2020-06-20T10:12:06Z" cacheDuration="PT604800S" entityID="https://ecm.sport80.com"><md:SPSSODescriptor AuthnRequestsSigned="true" WantAssertionsSigned="true" protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol"><md:KeyDescriptor use="signing"><ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#"><ds:X509Data><ds:X509Certificate><-- X509 Certificate --></ds:X509Certificate></ds:X509Data></ds:KeyInfo></md:KeyDescriptor><md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://ecm.sport80.com/saml/logout"/><md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</md:NameIDFormat><md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://ecm.sport80.com/saml/acs" index="1"/></md:SPSSODescriptor><md:Organization><md:OrganizationName xml:lang="en">Example</md:OrganizationName><md:OrganizationDisplayName xml:lang="en">Example</md:OrganizationDisplayName><md:OrganizationURL xml:lang="en">http://example.com</md:OrganizationURL></md:Organization><md:ContactPerson contactType="technical"><md:GivenName>Tech User</md:GivenName><md:EmailAddress>techuser@example.com</md:EmailAddress></md:ContactPerson><md:ContactPerson contactType="support"><md:GivenName>Support User</md:GivenName><md:EmailAddress>supportuser@example.com</md:EmailAddress></md:ContactPerson></md:EntityDescriptor>
AuthnRequest
To initiate login a AuthnRequest should be be sent to SingleSignOnService location detailed in the metadata. AuthnRequests should use the urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect binding. The request should contain a SAMLRequest parameter which is a deflated and base64 encoded XML authnRequest. All authnRequests should be singed. A Signature Parameter should contain the signature for the SAMLRequest. A SigAlg parameter should indicate which algorithm the signature uses. An optional RelayState parameter can be also included and will be returned with the response from the authnRquest.
Example AuthNRequest
<?xml version="1.0"?><AuthnRequest xmlns="urn:oasis:names:tc:SAML:2.0:protocol" ID="ONELOGIN_e6d35fd8e34cc782f5bde726be36ef8082018050" Version="2.0" IssueInstant="2020-06-18T09:28:46Z" Destination="http://auth.services.localhost/saml/login" ProtocolBinding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" AssertionConsumerServiceURL="http://localhost:9000/saml/acs" ProviderName="Example"><saml:Issuer xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion">https://ecm.sport80.com</saml:Issuer><NameIDPolicy Format="urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress" AllowCreate="false"/></AuthnRequest>
Example complete authnRequest url
http://auth.services.localhost/saml/login?SAMLRequest=fVJLbxoxEL7zK6K9s%2BvNsgQsQNoGkiJRQIHkkEvk2gNY8mPr8dLk39e7bmkbKZmbx%2FM95rMnyLSqadX4k3mAHw2g712FetXKIO0up0njDLUMJVLDNCD1nO6qbyt6nRJaO%2Bsttyp5B%2FscxRDBeWlNhC3n02SzXqw298v1SymGQ7gpB4JDMRhBUY4FE2I0IPmoAH5gYwKHUvBBhD6Bw8AzTQJt7GydPUsBbh1Up8nilelawW8dxAaWBj0zPiDINemTYT%2B%2F2eclJQUtyHOcm4cYpGG%2BIz55X9MsYyGiNLg%2BSw6YKsuZOln0WbtspuxRmot8F8gXaYQ0x89z%2BB6HkH7d77f97Wa3jyTVn3xurcFGg9tF4ceH1cXQxQIdE0KiD8YxmXUMk%2FZMu4XdrEVggADXKdbW%2BRFJudWT7N%2Bhv7Cattkt51urJH%2Fr%2Bm3dWaeZ%2F3ihPM27jhT9QzdKQTOpKiEcICYXnkop%2B%2FPWAfPhfbxrILnKZr1o5v%2BvOPsF&RelayState=http%3A%2F%2Flocalhost%3A9000%2F&SigAlg=http%3A%2F%2Fwww.w3.org%2F2001%2F04%2Fxmldsig-more%23rsa-sha512&Signature=JNQPIh2edUkHgy5HHO61VRWptNuIJC%2FKVhDXQDDccdVYuetKzent1cJVrAwQrVV4ZPymyNleRglNcbJjB7ldTf%2BbW6RlO6LRy35LUbo%2ByO4t32K83SS9r9U03%2Bp%2FCz9%2BKy6bYeDfhRyigjd4ACKcGx2ZfcyAXpA4WLisZ1%2FNboJ1soTCyTRJEIwUV5fB9cp2cNSa56P0R%2BQDlgHLr7pRrd%2BqQBqqr0nsFJhW4E9raw2szOl1venLHuXl8kejef0ZukIhTYgSriKeMOayRDHsjC1rksSrku5ahu%2BzAA9vhOS9IYeRj0iFXMj2Y8Rzv9VQcR%2FHNAuwZCS5e70TCm2xiA%3D%3DAuthnRequest Response
Once the user has been successfully authenticated a signed SAML Response with a signed Assertion will be sent back to the AssertionConsumerServiceURL which should use the urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST binding. The SAMLResponsewill be deflated and base64 encoded. The response will contain the users email as a attribute with a FriendlyName of email. It will also contain a UUID attribute what a FriendlyName of uuid. The UUID can then be used to query the API for user details. If request we can include a user API token that will allow you to query our API. This token is linked to the users session so upon logout the token will no longer be valid. You can access this token attribute with the FriendlyName of userApiToken
Example XML Response
<?xml version="1.0"?><samlp:Response xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" ID="_71b297f9e50fe39acea10853c1fc86f4653eefccc1" Version="2.0" IssueInstant="2020-06-18T14:31:30Z" Destination="https://ecm.sport80.com/saml/acs"><saml:Issuer xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion">https://sso.sport80.com</saml:Issuer><ds:Signature xmlns:ds="http://www.w3.org/2000/09/xmldsig#"><ds:SignedInfo><ds:CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/><ds:SignatureMethod Algorithm="http://www.w3.org/2000/09/xmldsig#rsa-sha512"/><ds:Reference URI="#_71b297f9e50fe39acea10853c1fc86f4653eefccc1"><ds:Transforms><ds:Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature"/><ds:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/></ds:Transforms><ds:DigestMethod Algorithm="http://www.w3.org/2001/04/xmlenc#sha512"/><ds:DigestValue>gRjkS5eXvRUru7RPw4y3JGyIQJobakLg2lPyD6eLwzk=</ds:DigestValue></ds:Reference></ds:SignedInfo><ds:SignatureValue>Al3KsupbEpKvZeAmnynOZTv2Nx49tUk5FH6Q6o6gCuMPmPQ73G0JVueNdgVSVt6h/B9VPY9qQNvjTArhLrhx3WV3vxgftkbwfRLLjPgO8vTrcSO2XPFTWrBm0tVdu1nzGbgi5ccm2sKZJAaL0268Tzt/oeHp4KysCXFVTpDqHv2L7BcLg1j4aghUAr/MmePmklK5lK6sEVJOquoDMfKgyzVFmTGZJW1v65+jPOZgLUfqUmkKptaOb0+/UBqqSEDV7MO6kR6xYef5IFiTwAmv8B78YNah02H3cfyDxqhhDQhPAErJgDEs7CtGlSFU7hqr6vID7yt6OmK1aE4dphF5Uw==</ds:SignatureValue><ds:KeyInfo><ds:X509Data><ds:X509Certificate><-- X509 Certificate --></ds:X509Certificate></ds:X509Data></ds:KeyInfo></ds:Signature><samlp:Status><samlp:StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:Success"/></samlp:Status><Assertion xmlns="urn:oasis:names:tc:SAML:2.0:assertion" ID="_db62dfa76e6ff9a2e41567e6fd63d6442221bd4090" Version="2.0" IssueInstant="2020-06-18T14:31:30Z"><Issuer>https://sso.sport80.com</Issuer><ds:Signature xmlns:ds="http://www.w3.org/2000/09/xmldsig#"><ds:SignedInfo><ds:CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/><ds:SignatureMethod Algorithm="http://www.w3.org/2000/09/xmldsig#sha512"/><ds:Reference URI="#_db62dfa76e6ff9a2e41567e6fd63d6442221bd4090"><ds:Transforms><ds:Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature"/><ds:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/></ds:Transforms><ds:DigestMethod Algorithm="http://www.w3.org/2001/04/xmlenc#sha512"/><ds:DigestValue>sVBGLobI0P93nvqwyp5yY+v8G84inFDLac4DB+cGYrs=</ds:DigestValue></ds:Reference></ds:SignedInfo><ds:SignatureValue>T1e++iIrVmy3l/NbS9dg+2knVOQTBJcPVwjZFdCdqlWoLRtlvaJkzESgBxfyqU2yx5JiCe/7NDNR1LvAmZ8ranru6TH062/nsLb/6uboZWn0rkr0uJXNp1PLtmG7G5RHSijFPSnPXhksmscEyvWC1alj+1JSPCgMMFklWTLHOXBWSi3D7QhahwvLynk6Wk23ksVzqmNsEK1DYd9EoSaIP9eabhGa+6zku+Rc+APE9mf2+/F7U/fsOVVQOXa5Ra3sRmQcaPjpMuw1JyaC2NBLVX5keqcRgSvsY3fCwyZaGVVa67hJXYfqpwLiPaWzHOWJg+4UPl2VvT1HxDEkzjw/Rw==</ds:SignatureValue><ds:KeyInfo><ds:X509Data><ds:X509Certificate><-- X509 Certificate --></ds:X509Certificate></ds:X509Data></ds:KeyInfo></ds:Signature><Subject><NameID Format="urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress">test@example.com</NameID><SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer"><SubjectConfirmationData InResponseTo="ONELOGIN_c53fbd4387389621d8d55f51cc6bd9fc019281b5" NotOnOrAfter="2020-06-18T14:32:30Z" Recipient="https://ecm.sport80.com/saml/acs"/></SubjectConfirmation></Subject><Conditions NotBefore="2020-06-18T14:31:30Z" NotOnOrAfter="2020-06-18T14:31:30Z"><AudienceRestriction><Audience>https://ecm.sport80.com</Audience></AudienceRestriction></Conditions><AttributeStatement><Attribute Name="email" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic" FriendlyName="email"><AttributeValue>test@example.com</AttributeValue></Attribute><Attribute Name="uuid" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic" FriendlyName="uuid"><AttributeValue>b11b4f62-f199-4c1b-b065-ba2be3f2b212</AttributeValue></Attribute></AttributeStatement><AuthnStatement AuthnInstant="2020-06-18T14:21:30Z" SessionIndex="k4i3jh9rfloaciidacaa3vc41n"><AuthnContext><AuthnContextClassRef>urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport</AuthnContextClassRef></AuthnContext></AuthnStatement></Assertion></samlp:Response>
Example response post body
SAMLResponse:"PD94bWwgdmVyc2lvbj0iMS4wIj8+CjxzYW1scDpSZXNwb25zZSB4bWxuczpzYW1scD0idXJuOm9hc2lzOm5hbWVzOnRjOlNBTUw6Mi4wOnByb3RvY29sIiBJRD0iXzc1OTc4NDFkODIzN2UwNjMxYTBmNTQzZjdkMDYzNDM2OTE0OWQ2MTFkZiIgVmVyc2lvbj0iMi4wIiBJc3N1ZUluc3RhbnQ9IjIwMjAtMDYtMThUMTM6MDg6MzJaIiBEZXN0aW5hdGlvbj0iaHR0cDovL2xvY2FsaG9zdDo5MDAwL3NhbWwvYWNzIj48c2FtbDpJc3N1ZXIgeG1sbnM6c2FtbD0idXJuOm9hc2lzOm5hbWVzOnRjOlNBTUw6Mi4wOmFzc2VydGlvbiI+aHR0cHM6Ly9zc28uc3BvcnQ4MC5jb208L3NhbWw6SXNzdWVyPjxkczpTaWduYXR1cmUgeG1sbnM6ZHM9Imh0dHA6Ly93d3cudzMub3JnLzIwMDAvMDkveG1sZHNpZyMiPgogIDxkczpTaWduZWRJbmZvPjxkczpDYW5vbmljYWxpemF0aW9uTWV0aG9kIEFsZ29yaXRobT0iaHR0cDovL3d3dy53My5vcmcvMjAwMS8xMC94bWwtZXhjLWMxNG4jIi8+CiAgICA8ZHM6U2lnbmF0dXJlTWV0aG9kIEFsZ29yaXRobT0iaHR0cDovL3d3dy53My5vcmcvMjAwMC8wOS94bWxkc2lnI3JzYS1zaGExIi8+CiAgPGRzOlJlZmVyZW5jZSBVUkk9IiNfNzU5Nzg0MWQ4MjM3ZTA2MzFhMGY1NDNmN2QwNjM0MzY5MTQ5ZDYxMWRmIj48ZHM6VHJhbnNmb3Jtcz48ZHM6VHJhbnNmb3JtIEFsZ29yaXRobT0iaHR0cDovL3d3dy53My5vcmcvMjAwMC8wOS94bWxkc2lnI2VudmVsb3BlZC1zaWduYXR1cmUiLz48ZHM6VHJhbnNmb3JtIEFsZ29yaXRobT0iaHR0cDovL3d3dy53My5vcmcvMjAwMS8xMC94bWwtZXhjLWMxNG4jIi8+PC9kczpUcmFuc2Zvcm1zPjxkczpEaWdlc3RNZXRob2QgQWxnb3JpdGhtPSJodHRwOi8vd3d3LnczLm9yZy8yMDAxLzA0L3htbGVuYyNzaGEyNTYiLz48ZHM6RGlnZXN0VmFsdWU+TGZ1NUs2YWJDZUdUTDNRbkh0dzQybC9JU01Kclh3WXpyeWxOZGFpTEl1bz08L2RzOkRpZ2VzdFZhbHVlPjwvZHM6UmVmZXJlbmNlPjwvZHM6U2lnbmVkSW5mbz48ZHM6U2lnbmF0dXJlVmFsdWU+TTc1bG56VGN2SUQ1RUpDR1lzMjVOalJ5U1BkY0JsQUtpcFh0N0VjcTZuczMxdkpOVW9XR0NKTGx5SkczWWdjd016L3ZEMWhmSU0wV3lod1pWTDhBb0VJdm5aRVVFNGt6V3Y4TnE1VkdvREQwSDJoUWhjeXlSbWdVbnBGNC8zVzZNbzcwT0w5SldVQXlFVno3NDIxVk5ITm0yc0FlTFJ2amI2a01kKzdiaVIrZkZ1dEJCbVZWT3pTUjFtMEx2VUNrOERiM2k4blB6T0Z4QWluM3VQV2o5N2tEeGxMeVJiNHptRzZZbjBnbVY4clZiM1M5ZHFDOCsvdVFYM09QMTVzK1BOTnpNYkJ2c1NRaGg3Q3RXS0FndWZpbmd3WFAxaVlWOGFnV2thVW1DMWpIbWV3RCtGYkJpSHR6MEQ5M28vaWs5TWtyNll2OS8yci9ZTGNUTktMcm53PT08L2RzOlNpZ25hdHVyZVZhbHVlPgo8ZHM6S2V5SW5mbz48ZHM6WDUwOURhdGE+PGRzOlg1MDlDZXJ0aWZpY2F0ZT5NSUlFQVRDQ0F1bWdBd0lCQWdJVWJqTmxvTTdlMzhOZ3JtNW5JdTNUaFlhUlFrNHdEUVlKS29aSWh2Y05BUUVOQlFBd2dZOHhDekFKQmdOVkJBWVRBa2RDTVJnd0ZnWURWUVFJREE5VGIzVjBhQ0JaYjNKcmMyaHBjbVV4RWpBUUJnTlZCQWNNQ1ZOb1pXWm1hV1ZzWkRFUU1BNEdBMVVFQ2d3SFUzQnZjblE0TURFTk1Bc0dBMVVFQ3d3RVZHVmphREVRTUE0R0ExVUVBd3dIVTNCdmNuUTRNREVmTUIwR0NTcUdTSWIzRFFFSkFSWVFkR1ZqYUVCemNHOXlkRGd3TG1OdmJUQWVGdzB5TURBek1UZ3hNak0xTXpCYUZ3MHlNVEF6TVRneE1qTTFNekJhTUlHUE1Rc3dDUVlEVlFRR0V3SkhRakVZTUJZR0ExVUVDQXdQVTI5MWRHZ2dXVzl5YTNOb2FYSmxNUkl3RUFZRFZRUUhEQWxUYUdWbVptbGxiR1F4RURBT0JnTlZCQW9NQjFOd2IzSjBPREF4RFRBTEJnTlZCQXNNQkZSbFkyZ3hFREFPQmdOVkJBTU1CMU53YjNKME9EQXhIekFkQmdrcWhraUc5dzBCQ1FFV0VIUmxZMmhBYzNCdmNuUTRNQzVqYjIwd2dnRWlNQTBHQ1NxR1NJYjNEUUVCQVFVQUE0SUJEd0F3Z2dFS0FvSUJBUUMycllIWUx6Q0tockFrSmlEY1A0aW1NNDhadDlyVFpsdlpqMkhoODFZbkp4RDFoUy9BbTlaeGZJRFM0L0tkMmRVZjZUdXFxK1k4cFNrT3gxcE9Hc2x0VDcwYUJwV1htbEVXT21qTEF3aldYblZSeGZHeUtZMHJNQXkvZkdFcXRpckgrUkdiWG8vN1BlRHdqZzlmWldiYzg5c0N0eVBaV3oxeVd6MnQybVE4aHpvUCtKYTIwVlkydDVlSmVjMG9ZOS9Wc0s4dEpDODBYWmxEd2lVcEI3L3J0RHB4c2VWR3hYN04yL01IR1RjT3crcDV3RXY0Z01WbTNUcWFpa2VpNi9wNEJNeEZWSXdTMXdCOU5PWlpKc3c5NkhxWXJqUWZ4dmpCTHorQ0VZeXVkdDUyYS9lSVlPcG9hckNDYmtkVzZKaVhVNmZtSUttOWI3WWx0TFNXcm5GL0FnTUJBQUdqVXpCUk1CMEdBMVVkRGdRV0JCUjFHTVl6b1BLaS9wY0p3MDJyL3dGNzA5M2xJVEFmQmdOVkhTTUVHREFXZ0JSMUdNWXpvUEtpL3BjSncwMnIvd0Y3MDkzbElUQVBCZ05WSFJNQkFmOEVCVEFEQVFIL01BMEdDU3FHU0liM0RRRUJEUVVBQTRJQkFRQmx6TDViajRhNUczeTFwNk93RHBQcEUrVXNLT1BDRGlDcDZoYW5SMnhYTnF3QTF3aEZPbklMeW0zYzloeEhTQ3hZNDdOblBMVjZTUWlYelkvOU9lZElwVk5VR0pGTVhDTmFvWkUzZmRnY3hyNTlCdmpyMmgvRGdEWkszWFkycEx1Z0htM1FFUDMwM09ZYm1pcW11QWhoRlBLZTFLb2x0MTBpanhVblVUb3pKeXdZVTJvV0dmeVZUTjk0YlFWODJHVUFQV2hsY01DcmU4L2c0ZnBUOGNCUURKbFB6VExld2VCWW8xMXhLc1h3WmIwMmc4cGtadXBIa283Ym5qQTJEOUc3aytsc0s4RXpOOFMyZXBSVkZwaHc4MHR3dlNNQU0wMVpTUlhmZndQako5WXRBVWtyaytsYmlxWm11K1J2YTBlZC9SMndvUGtxUEx3K2MrN2gvWVk2PC9kczpYNTA5Q2VydGlmaWNhdGU+PC9kczpYNTA5RGF0YT48L2RzOktleUluZm8+PC9kczpTaWduYXR1cmU+PHNhbWxwOlN0YXR1cz48c2FtbHA6U3RhdHVzQ29kZSBWYWx1ZT0idXJuOm9hc2lzOm5hbWVzOnRjOlNBTUw6Mi4wOnN0YXR1czpTdWNjZXNzIi8+PC9zYW1scDpTdGF0dXM+PEFzc2VydGlvbiB4bWxucz0idXJuOm9hc2lzOm5hbWVzOnRjOlNBTUw6Mi4wOmFzc2VydGlvbiIgSUQ9Il82MmU0MmNmZTk0MTQ2Y2I2NWNlNmRhODNmOTM4YjczZTFkNzI3MzZhNzAiIFZlcnNpb249IjIuMCIgSXNzdWVJbnN0YW50PSIyMDIwLTA2LTE4VDEzOjA4OjMyWiI+PElzc3Vlcj5odHRwczovL3Nzby5zcG9ydDgwLmNvbTwvSXNzdWVyPjxkczpTaWduYXR1cmUgeG1sbnM6ZHM9Imh0dHA6Ly93d3cudzMub3JnLzIwMDAvMDkveG1sZHNpZyMiPgogIDxkczpTaWduZWRJbmZvPjxkczpDYW5vbmljYWxpemF0aW9uTWV0aG9kIEFsZ29yaXRobT0iaHR0cDovL3d3dy53My5vcmcvMjAwMS8xMC94bWwtZXhjLWMxNG4jIi8+CiAgICA8ZHM6U2lnbmF0dXJlTWV0aG9kIEFsZ29yaXRobT0iaHR0cDovL3d3dy53My5vcmcvMjAwMC8wOS94bWxkc2lnI3JzYS1zaGExIi8+CiAgPGRzOlJlZmVyZW5jZSBVUkk9IiNfNjJlNDJjZmU5NDE0NmNiNjVjZTZkYTgzZjkzOGI3M2UxZDcyNzM2YTcwIj48ZHM6VHJhbnNmb3Jtcz48ZHM6VHJhbnNmb3JtIEFsZ29yaXRobT0iaHR0cDovL3d3dy53My5vcmcvMjAwMC8wOS94bWxkc2lnI2VudmVsb3BlZC1zaWduYXR1cmUiLz48ZHM6VHJhbnNmb3JtIEFsZ29yaXRobT0iaHR0cDovL3d3dy53My5vcmcvMjAwMS8xMC94bWwtZXhjLWMxNG4jIi8+PC9kczpUcmFuc2Zvcm1zPjxkczpEaWdlc3RNZXRob2QgQWxnb3JpdGhtPSJodHRwOi8vd3d3LnczLm9yZy8yMDAxLzA0L3htbGVuYyNzaGEyNTYiLz48ZHM6RGlnZXN0VmFsdWU+NmJRNVQxc1RBd2FWOGNnM1hUUXdoRHRhdEYrdUVzU1gwZW5GL0JiTitXOD08L2RzOkRpZ2VzdFZhbHVlPjwvZHM6UmVmZXJlbmNlPjwvZHM6U2lnbmVkSW5mbz48ZHM6U2lnbmF0dXJlVmFsdWU+dFVEZEY3ZzFHNm5xbTVZZlliYmk5WGwxZ01RU1ZNdU9KRXhac1lQOHZrVjhxUVQrOHVNV2doZFRHcEVYdkhseERncVdkVVVEZ3RmMkttZDR6K0VOU3NOY3pDNm56U3Q5bHR6My9TZkxsQjluT0J1ZkwwNlI2bmJXWmo4VzU3QWtPYnJxaGJKbmNqYkxDaitxUjZTeGFaWFp2Y2dHNlFrYm0rT0QrOXlteXY0eXNENms2a2t6amc2V3RZMVVjYXAvcWhIbWR0UTVxSlBWYlJ5L0MxYVM1VUhRV2d2S0VLd2hpWG9CSDQ2MTZ0TFFKMkdxNkhGUTRGRmNhUCswaW5EcEdEeE4wSFcwOFZQV3phKzNYWDlxR0RLQitkWHJvaENVaDg4andya3lmaEQ4TlI3VGVIRUU5eGxuL3V6U3pzSmYrdDg4eXM2YkFIMjZlbXFNMElWTjJRPT08L2RzOlNpZ25hdHVyZVZhbHVlPgo8ZHM6S2V5SW5mbz48ZHM6WDUwOURhdGE+PGRzOlg1MDlDZXJ0aWZpY2F0ZT5NSUlFQVRDQ0F1bWdBd0lCQWdJVWJqTmxvTTdlMzhOZ3JtNW5JdTNUaFlhUlFrNHdEUVlKS29aSWh2Y05BUUVOQlFBd2dZOHhDekFKQmdOVkJBWVRBa2RDTVJnd0ZnWURWUVFJREE5VGIzVjBhQ0JaYjNKcmMyaHBjbVV4RWpBUUJnTlZCQWNNQ1ZOb1pXWm1hV1ZzWkRFUU1BNEdBMVVFQ2d3SFUzQnZjblE0TURFTk1Bc0dBMVVFQ3d3RVZHVmphREVRTUE0R0ExVUVBd3dIVTNCdmNuUTRNREVmTUIwR0NTcUdTSWIzRFFFSkFSWVFkR1ZqYUVCemNHOXlkRGd3TG1OdmJUQWVGdzB5TURBek1UZ3hNak0xTXpCYUZ3MHlNVEF6TVRneE1qTTFNekJhTUlHUE1Rc3dDUVlEVlFRR0V3SkhRakVZTUJZR0ExVUVDQXdQVTI5MWRHZ2dXVzl5YTNOb2FYSmxNUkl3RUFZRFZRUUhEQWxUYUdWbVptbGxiR1F4RURBT0JnTlZCQW9NQjFOd2IzSjBPREF4RFRBTEJnTlZCQXNNQkZSbFkyZ3hFREFPQmdOVkJBTU1CMU53YjNKME9EQXhIekFkQmdrcWhraUc5dzBCQ1FFV0VIUmxZMmhBYzNCdmNuUTRNQzVqYjIwd2dnRWlNQTBHQ1NxR1NJYjNEUUVCQVFVQUE0SUJEd0F3Z2dFS0FvSUJBUUMycllIWUx6Q0tockFrSmlEY1A0aW1NNDhadDlyVFpsdlpqMkhoODFZbkp4RDFoUy9BbTlaeGZJRFM0L0tkMmRVZjZUdXFxK1k4cFNrT3gxcE9Hc2x0VDcwYUJwV1htbEVXT21qTEF3aldYblZSeGZHeUtZMHJNQXkvZkdFcXRpckgrUkdiWG8vN1BlRHdqZzlmWldiYzg5c0N0eVBaV3oxeVd6MnQybVE4aHpvUCtKYTIwVlkydDVlSmVjMG9ZOS9Wc0s4dEpDODBYWmxEd2lVcEI3L3J0RHB4c2VWR3hYN04yL01IR1RjT3crcDV3RXY0Z01WbTNUcWFpa2VpNi9wNEJNeEZWSXdTMXdCOU5PWlpKc3c5NkhxWXJqUWZ4dmpCTHorQ0VZeXVkdDUyYS9lSVlPcG9hckNDYmtkVzZKaVhVNmZtSUttOWI3WWx0TFNXcm5GL0FnTUJBQUdqVXpCUk1CMEdBMVVkRGdRV0JCUjFHTVl6b1BLaS9wY0p3MDJyL3dGNzA5M2xJVEFmQmdOVkhTTUVHREFXZ0JSMUdNWXpvUEtpL3BjSncwMnIvd0Y3MDkzbElUQVBCZ05WSFJNQkFmOEVCVEFEQVFIL01BMEdDU3FHU0liM0RRRUJEUVVBQTRJQkFRQmx6TDViajRhNUczeTFwNk93RHBQcEUrVXNLT1BDRGlDcDZoYW5SMnhYTnF3QTF3aEZPbklMeW0zYzloeEhTQ3hZNDdOblBMVjZTUWlYelkvOU9lZElwVk5VR0pGTVhDTmFvWkUzZmRnY3hyNTlCdmpyMmgvRGdEWkszWFkycEx1Z0htM1FFUDMwM09ZYm1pcW11QWhoRlBLZTFLb2x0MTBpanhVblVUb3pKeXdZVTJvV0dmeVZUTjk0YlFWODJHVUFQV2hsY01DcmU4L2c0ZnBUOGNCUURKbFB6VExld2VCWW8xMXhLc1h3WmIwMmc4cGtadXBIa283Ym5qQTJEOUc3aytsc0s4RXpOOFMyZXBSVkZwaHc4MHR3dlNNQU0wMVpTUlhmZndQako5WXRBVWtyaytsYmlxWm11K1J2YTBlZC9SMndvUGtxUEx3K2MrN2gvWVk2PC9kczpYNTA5Q2VydGlmaWNhdGU+PC9kczpYNTA5RGF0YT48L2RzOktleUluZm8+PC9kczpTaWduYXR1cmU+PFN1YmplY3Q+PE5hbWVJRCBGb3JtYXQ9InVybjpvYXNpczpuYW1lczp0YzpTQU1MOjEuMTpuYW1laWQtZm9ybWF0OmVtYWlsQWRkcmVzcyI+Y2hyaXMuam9obnN0b25Ac3BvcnQ4MC5jb208L05hbWVJRD48U3ViamVjdENvbmZpcm1hdGlvbiBNZXRob2Q9InVybjpvYXNpczpuYW1lczp0YzpTQU1MOjIuMDpjbTpiZWFyZXIiPjxTdWJqZWN0Q29uZmlybWF0aW9uRGF0YSBJblJlc3BvbnNlVG89Ik9ORUxPR0lOX2M3ZmM3YjkwNzZlOWNiNDc3MjRlMzQyODE2NDdkOTE4NTdiZjQ0MjAiIE5vdE9uT3JBZnRlcj0iMjAyMC0wNi0xOFQxMzowOTozMloiIFJlY2lwaWVudD0iaHR0cDovL2xvY2FsaG9zdDo5MDAwL3NhbWwvYWNzIi8+PC9TdWJqZWN0Q29uZmlybWF0aW9uPjwvU3ViamVjdD48Q29uZGl0aW9ucyBOb3RCZWZvcmU9IjIwMjAtMDYtMThUMTM6MDg6MzJaIiBOb3RPbk9yQWZ0ZXI9IjIwMjAtMDYtMThUMTM6MDg6MzJaIj48QXVkaWVuY2VSZXN0cmljdGlvbj48QXVkaWVuY2U+aHR0cHM6Ly9lY20uc3BvcnQ4MC5jb208L0F1ZGllbmNlPjwvQXVkaWVuY2VSZXN0cmljdGlvbj48L0NvbmRpdGlvbnM+PEF0dHJpYnV0ZVN0YXRlbWVudD48QXR0cmlidXRlIE5hbWU9Imh0dHA6Ly9zY2hlbWFzLnhtbHNvYXAub3JnL3dzLzIwMDUvMDUvaWRlbnRpdHkvY2xhaW1zL2VtYWlsYWRkcmVzcyIgRnJpZW5kbHlOYW1lPSJlbWFpbCI+PEF0dHJpYnV0ZVZhbHVlPmNocmlzLmpvaG5zdG9uQHNwb3J0ODAuY29tPC9BdHRyaWJ1dGVWYWx1ZT48L0F0dHJpYnV0ZT48QXR0cmlidXRlIE5hbWU9Imh0dHA6Ly9zY2hlbWFzLnhtbHNvYXAub3JnL3dzLzIwMDUvMDUvaWRlbnRpdHkvY2xhaW1zL3ByaXZhdGVwZXJzb25hbGlkZW50aWZpZXIiIEZyaWVuZGx5TmFtZT0icHBpZCI+PEF0dHJpYnV0ZVZhbHVlPjVlZWI2NzUwMTA0OTQ8L0F0dHJpYnV0ZVZhbHVlPjwvQXR0cmlidXRlPjwvQXR0cmlidXRlU3RhdGVtZW50PjxBdXRoblN0YXRlbWVudCBBdXRobkluc3RhbnQ9IjIwMjAtMDYtMThUMTI6NTg6MzJaIiBTZXNzaW9uSW5kZXg9Img5N2gxcG1wa2txYjYzMmxsdm50NmZobThlIj48QXV0aG5Db250ZXh0PjxBdXRobkNvbnRleHRDbGFzc1JlZj51cm46b2FzaXM6bmFtZXM6dGM6U0FNTDoyLjA6YWM6Y2xhc3NlczpQYXNzd29yZFByb3RlY3RlZFRyYW5zcG9ydDwvQXV0aG5Db250ZXh0Q2xhc3NSZWY+PC9BdXRobkNvbnRleHQ+PC9BdXRoblN0YXRlbWVudD48L0Fzc2VydGlvbj48L3NhbWxwOlJlc3BvbnNlPgo="RelayState:"http://ecm.sport80.com/dashboard"
Single Logout (SLO)
Your SLO endpoint needs to be able to send a SAML Logout Request to our SLO endpoint. This will then log the user out of all active SSO sessions. All SLO requests need to be singed.
Your SLO endpoint needs to be able to handle SAML Logout Requests. This is to ensure that when a user is logged out they are logged out of all systems. You should terminate the users session before sending the SLO request.
All SLO Requests should be sent to the SingleLogoutService location details in the metadata. It should use the urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect binding.
Example XML Logout Request
<samlp:LogoutRequest xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" ID="ONELOGIN_21df91a89767879fc0f7df6a1490c6000c81644d" Version="2.0" IssueInstant="2014-07-18T01:13:06Z" Destination="http://idp.example.com/SingleLogoutService.php"><saml:Issuer>http://sp.example.com/demo1/metadata.php</saml:Issuer><saml:NameID SPNameQualifier="http://sp.example.com/demo1/metadata.php" Format="urn:oasis:names:tc:SAML:2.0:nameid-format:transient">ONELOGIN_f92cc1834efc0f73e9c09f482fce80037a6251e7</saml:NameID></samlp:LogoutRequest>
Example Logout URL
https://sso.sport80.com/saml/logout?SAMLRequest=fZJfa8IwFMXf%2FRTSd9uk1VqDFgS3UXAKc%2BxhLyNNUxvIn5qbih9%2FsXXghC2PJ%2Bd3bs4lS6BKtmRrjqZzb%2FzUcXCjsT8XJTWQ%2FnYVdFYTQ0EA0VRxII6Rw%2Fp1S%2BIQkdYaZ5iRwQP2P0UBuHXC6AErNqtgv3va7l%2BK3VdKp5jVWYrxIsF1gssZwnWdxtirJY1pVlLM5otyQD%2B4BZ%2BzCnzsLQyg44UGR7XzMorRBKUTnL3jhMwSgtLPwbfxXYWmrqcb51oSRbRzTeifdhaMQygNo7Ix4KJro0j2Wwrynl5eJdLPsvmVBo9zpkJojXUZCplRy%2BjedIft%2FEKKzfjZWEXd35vCIe4VUU3q3kq4okKuq8pygCBnjRVwGzJE3g1pycGbfLlCV%2FySz5Exp2OtSiE7AWra8iw51m52ng4BD%2FbRj%2Frra%2BTf&RelayState=http%3A%2F%2Flocalhost%3A9000%2Fsaml%2Flogout&SigAlg=http%3A%2F%2Fwww.w3.org%2F2001%2F04%2Fxmldsig-more%23rsa-sha512&Signature=U917buZRvMx29iMS88JpxbtzG70K1D%2Bg0HUKjpDAW0oFexoa3e1dNjsdw1DU765RId%2FQ3iz9m4eSkxXs%2F8vvfcBukXMOxgFV55RHq%2Bmh%2BsStiGKKjE6ZFF4p0aTrNLuQc9s7ZsiTZj1gm8saMuzGYh6IUh2d0hBDW54oYIgMjktqMko4glCtaj6u7GMDC4JErcxxOY4qfGrupAEMBGMqMXOfCekwQksG6N3Y%2BvW6SXZ7Q9uK7FnWDR7GhYimMGs6%2FYF%2FPscJEOOO6JTird8BptvqZXBVv1QI9DYS9aLCYvSts0wfMq%2BbGGVtqU2hghkYhiOLRH693RCFCs3LvLcJ8Q%3D%3D